September Update: 2016 Presidential Election Prediction
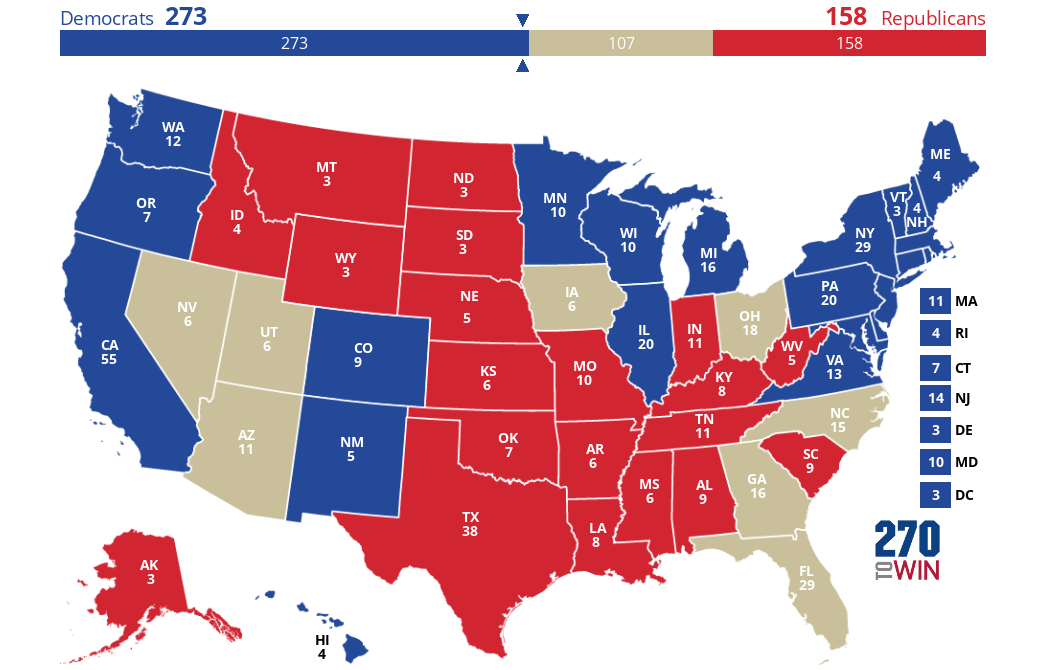
 Let’s take another look at state-by-state polling and state voting history to get a good prediction for the 2016 election. I primarily look at the RCP average polling numbers but I also take into account polls they don’t use if data is lacking for a state. So taking all that into account, not much has changed from my last prediction.
Let’s take another look at state-by-state polling and state voting history to get a good prediction for the 2016 election. I primarily look at the RCP average polling numbers but I also take into account polls they don’t use if data is lacking for a state. So taking all that into account, not much has changed from my last prediction.
I think Clinton will get at least 279 electoral votes, Trump at least 180 and 79 electoral votes are still up for grabs. With Clinton still reaching 270 at a minimum, this would still place her in the White House. Trump would need to put another state in contention where Clinton still has a lead and gain that in addition to the other states I consider in contention to win. That is still a long shot for his campaign.
Now for the potential spoilers, both Governor Gary Johnson (L) and Jill Stein (G) will be on the ballot in most states in 2016. The Libertarian Party is on the ballot in all 50 states while the Green Party will be on many of them but missed crucial deadlines for states like Arizona. In polls where Governor Gary Johnson and Jill Stein were included, the polling gap between Clinton and Trump narrowed. Johnson has been polling in double digits in 42 states while Jill Stein has been polling at around 3-5%. This really only comes into play if Jill Stein can spoil a state for Clinton or Johnson gains enough momentum to take a state from Clinton like New Mexico, where he was a successful Governor. If that happened the election could potentially go to Congress where things would become very interesting but that is as much of long shot as Trump winning the election at this point.
September Update: 2016 Presidential Election Prediction Read Post »

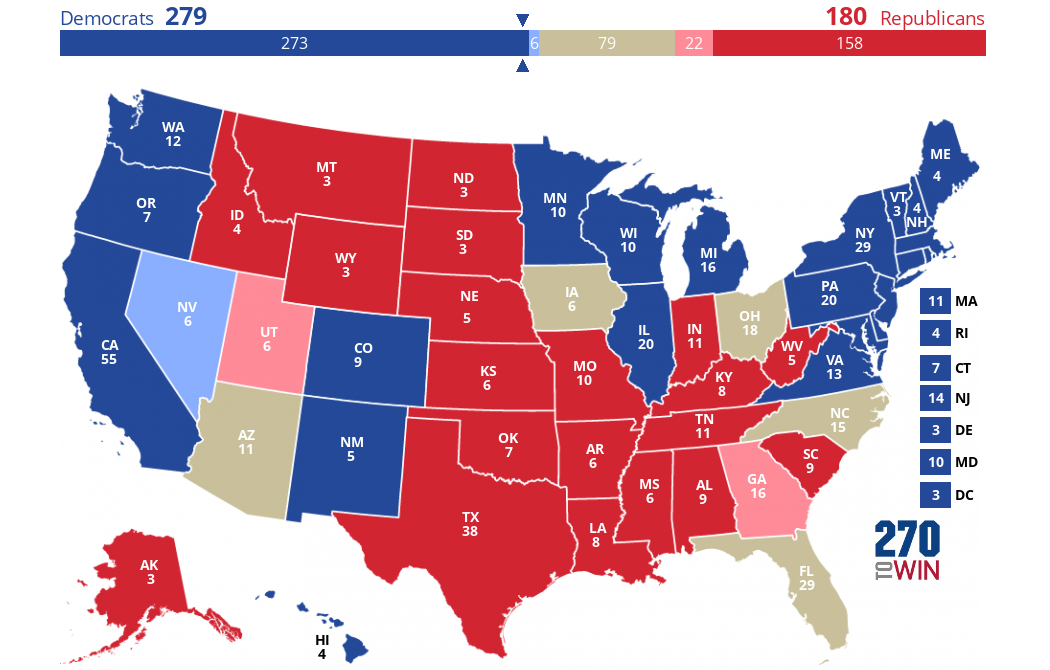
 Click the map to create your own at
Click the map to create your own at